Screening Room
The Authenticity Institute
Wes Kussmaul's
Lecture Series
FIRST, how we got into this mess: Evolution of the natural concept of authenticity from the earliest villages through feudal kingdoms, the wild west, the telephone age, the dot-com bust, and into the critical INAUTHENTICITY crisis now facing our global village of billions.
THEN, how we are going to get out of it: The nuts and bolts of the AUTHENTICITY INFRASTRUCTURE – our name for "PKI Done Right" – based on the marriage of time-tested real-world concepts with brilliant technology that has been lying dormant for decades.
"On the Internet, nobody knows you're a dog."
Dog cartoon ©1993 Peter Steiner, The New Yorker Collection / The Cartoon Bank
Side trip:
Side trip:
(Watch in this order)
More Videos
Assorted topics (alphabetical by title)
Digital signatures beyond blockchain
Adding ACCOUNTABILITY to blockchains
For thought leaders, world-watchers, and entrepreneurs
Watching the daily headlines
[Moved to Back Room]
Doing business by the roadside
The big business of breeding personal data
Invaders in your "information home"
The "DNA" of Authenticity
What does "Done Right" mean?
Introducing Duly Constituted Public Authority
Quick rundown of this "Foundation of Security"
Why PKI hasn't delivered on its promise (yet)
Ten Reasons in more detail
Surprising PKI parallel in skyscraper history
A first look at what it's about and PKI's role
Real security is rooted in common sense
2:22
11:10
2:14
8:41
9:27
5:11
3:04
6:46
6:23
8:24
6:27
2:58
9:02
5:42
12:00
2:49
1:52
8:33
9:40
6:44
8:30
8:22
2:40
14:13
10:13
6:40
9:55
10:04
4:23
10:51
6:35
Side trip:
Wes Kussmaul's
United Nations Speech
Introducing Authenticity, PKI, The City of Osmio, and Duly Constituted Public Authority at the 2008 United Nations World Summit On Information Society
10:36
Stories
How we
got here
Personal accounts narrated by Wes
A wrong turn 30 years ago
Bringing back ACCOUNTABLE ANONYMITY
4:41
4:11
6:28
4:26
Why security technology has failed us
Wasn't PKI supposed to fix all that?
View as thumbnails
Wordwide Duly Constituted Public Authority
4:00
32:54
5:41
2:31
NOT the same as "electronic" signatures!
Knowing WHO is in your space
1:22
Digital signatures take aim at fake news
2:02
Doing nothing is not an option
9:07
A big problem requires a big change
2:20
Own your information and license it to others
4:47
The history and mission of The City of Osmio
5:23
Digital signatures with ACCOUNTABILITY
4:01
A new coalition of time-tested ingredients
1:58
Chalkboard breakdown of the math
1:15
The meaning of MEASURABLY RELIABLE
5:02
A looming global banking threat
3:32
3:32
8:10
Turning classic PKI into full-blown Authenticity™
Master access to your connected world
3:28
3:20
A Brief Authenticity overview for new members
1:30
Adding ACCOUNTABILITY with digital signatures
PKI-secured identity eliminates two-factor hacks
2:11
7:51
Genesis of the Authenticity™ vision
7:51
Genesis of the Authenticity™ vision
4:21
2:16
8:14
1:54
8:29
0:42
1:57
6:11
1:26
3:09
2:32
2:55
Simple concept, transformative power
(Formerly PKI Revealed)
1:58
(Includes "Synthetic Identites" video)
Expanding personal ACCOUNTABILITY
4:47
PKI - The forgotten construction material
4:01
Hiding In Plain Sight
From AC to Authentiverse
1:00
Evolution
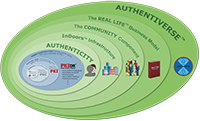
Authentiverse Series
Back Room
Attestation Officers
1:46
Top of Wallet
2:33
Ovals see Evolution
Series starting points
MOI - MyOwnInformation
Your personal information vault
Accountability Anonymity
7:58
"The ovals"
ABE - see What is ABE?
PKI Revealed - see What is PKI?
AC - see How AC Works
How AC Works
Simple concept - TRANSFORMATIVE power
1:53
What is ABE?
Accountability-Based Environment
3:19
Authenticity in a Nutshell
CTBG vs. ABE before they were called that
CTBG vs. ABE see also Authenticity In a Nutshell
A brief overview
1:50
CTBG vs. ABE with "Learn more" at end
A brief overview
1:50
CTBG vs. ABE
Videos about Osmio
List of videos containing information about the City of Osmio
View/download list
1:33
Tunnel Vision
Where is the REAL threat?
(In the Back Room)
Authenticity – Start Here
Three big ideas
3:02
[This needs to be moved up to where it belongs in the Lecture Series list]
NEW
Videos playable by Jitsi "Share video"
Copy/paste the URL in the "Share video" box
(More coming)
https://www.taivideos.com/authenticity-start-here-260125.mp4
https://www.taivideos.com/authenticity-quick-tour-260125.mp4
NEW
Authenticity – Start Here
A Very Quick Tour of Authenticity
Fake News – see Reporter's Credential
https://www.taivideos.com/deep-fakes_260130.mp4
Deep Fakes
The solution has been HIDING IN PLAIN SIGHT
Deep Fakes
4:23